from Virus alerts
April 29, 2016
April 2016 began with a new version of the Gozi Trojan, which now could create peer-to-peer botnets. Later this month, cybercriminals started to spread a backdoor for Linux via a hacker utility. Besides, security researchers detected the intensified activity of Internet scammers who have already tricked a big number of gullible users by creating fake online stores.
PRINCIPAL TRENDS IN APRIL
- New version of the Gozi Trojan
- New backdoor for Linux
- Intensified activity of Internet scammers
Threat of the month
Instead of contriving brand new banking Trojans, attackers prefer to modify old versions of popular financial malware programs—for example, Trojan.Gozi, which is able to carry out a wide range of malicious activities: it can steal information entered by the user into web data forms and perform web injections and keylogging functions. In addition, the Trojan is also designed to get remote access to the user’s machine by means of Virtual Network Computing (VNC). Moreover, upon a command, the Trojan can run the SOCKS proxy server and download and install various plug-ins.

However, unlike its counterparts, Trojan.Gozi can also generate peer-to peer (P2P) botnets, which allows the Trojan to transmit encrypted information directly to the infected machines. You can find more about this malware program in the news article published by Doctor Web.
According to statistics collected by Dr.Web CureIt!

-
Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications.
-
A malware family that can modify the home page in the browser settings.
-
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition to this, the malware can replace advertisements displayed on different Internet resources.
-
A family of malicious programs designed to download other malware to the compromised computer.
According to Doctor Web statistics servers
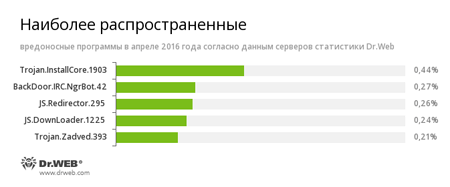
-
Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications.
-
A fairly common Trojan, which is known to information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machine controlled by cybercriminals via the IRC (Internet Relay Chat) text-messaging protocol.
-
JS.Redirector
A family of malicious scripts that are written in JavaScript and designed to redirect users to different (including malicious and fraudulent) webpages.
-
JS.Downloader
A family of malicious scripts that are written in JavaScript and designed to download and install other malware programs on the computer.
-
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites.
Statistics concerning malicious programs discovered in email traffic

-
JS.Downloader
A family of malicious scripts that are written in JavaScript and designed to download and install other malware programs on the computer.
-
Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications.
-
Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.
Encryption ransomware

Trojan.Encoder.858 is the most frequently detected Trojan in April 2016.
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention |
 |
 |
Dangerous websites
During April 2016, Doctor Web added 749,173 URLs into the Dr.Web database of non-recommended sites.
| March 2016 |
April 2016 |
Dynamics |
| +458,013 |
+749,173 |
+63.6% |
April witnessed a big number of Internet users who fell victim to online shopping scams. Numerous fake online stores have all the typical features of real online shops. Yet, web design of these fraudulent websites is always identical.

To learn more about how this scheme of online shopping fraud works, refer to the article.
Other threats
To illegally infiltrate computer systems and remote networks, attackers often use software vulnerabilities. Yet, incorrect configurations of server applications and other programs may pose a more dangerous threat. In April, Doctor Web specialists discovered some misconfiguration of hardware belonging to a large company that supplies DNS and web hosting services. Thus, its clients revealed a list of their registered subdomains—in particular, ones for internal use— to the world. These domains can be used to organize internal non-public servers, version control systems (VCS), bug trackers, various monitoring services, wiki resources, etc. Having this domain list, attackers can easily examine the network of a potential victim in order to find vulnerabilities. For more details, refer to the article.
Furthermore, Doctor Web security researchers detected a new backdoor for Linux—Linux.BackDoor.Xudp.1. Its key feature lies in the fact that it infiltrated the system via some hacker utility designed to send out UDP packets to a specified address. It means that the Linux user, in their attempts to attack a server, fell victim to the Trojan.
Security researchers registered that Linux.BackDoor.Xudp.1 can continuously send various requests to the specified remote server, carry out DDoS attacks, and execute arbitrary commands. In addition, it can scan ports within a specified range of IP addresses, run certain files, send any file to cybercriminals, and execute other functions. All the features of this Trojan are described in our review.
In the end of the month, security researchers detected Trojan.BPlug.1074, a malware program masquerading as a plug-in for Google Chrome which sent out spam messages to Facebook users. This Trojan was used to distribute other dangerous extensions for Chrome. As of April 29, 2016, more than 12,000 Facebook users have already fallen victim to Trojan.BPlug.1074. For more about this incident, refer to the news article.
Malicious and unwanted programs for mobile devices
According to the statistics collected by Dr.Web for Android, aggressive advertising modules became the most frequently detected programs among other malicious and unwanted applications in April. Such modules are often designed not only to display annoying advertisements but also to steal confidential information and to download and install various software, which helps cybercriminals make money from victims. In addition, a new Trojan named Android.GPLoader.1.origin, which was designed to covertly install other applications, was detected in the past month.
Among the most noticeable April events related to mobile malware, we can mention
- Increase in activity of aggressive advertising modules for Android.
- Emergence of a new Trojan that covertly installs various software.
Find out more about malicious and unwanted programs for mobile devices in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live
