http://www.welivesecurity.com/2015/07/30/operation-potao-express/
http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf
TL; DR
------------------------------------------------------------------------------------------------------------------------
Original
Attack Timeline

Trojanized TrueCrypt
http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf
TL; DR
2011- July 2015
- aka Sapotao and node69
- Group - Sandworm / Quedagh APT
- Vectors - USB, exe as doc, xls
- Victims - RU, BY, AM, GE
- Victims - MMM group, UA gov
- truecryptrussia.ru has been serving modified versions of the encryption software (Win32/FakeTC) that included a backdoor to selected targets.
- Win32/FakeTC - data theft from encrypted drives
- The Potao main DLL only takes care of its core functionality; the actual spying functions are implemented in the form of downloadable modules. The plugins are downloaded each time the malware starts, since they aren’t stored on the hard drive.
- 1st Full Plugin and its export function is called Plug. Full plugins run continuously until the infected system is restarted
- 2nd Light Plugin with an export function Scan. Light plugins terminate immediately after returning a buffer with the information they harvested off the victim’s machine.
- Some of the plugins were signed with a certificate issued to “Grandtorg”:
- Traffic
- Strong encryption. The data sent is encapsulated using the XML-RPC protocol.
- MethodName value 10a7d030-1a61-11e3-beea-001c42e2a08b is always present in Potao traffic.
- After receiving the request the C&C server generates an RSA-2048 public key and signs this generated key with another, static RSA-2048 private key .
- In 2nd stage the malware generates a symmetric AES-256 key. This AES session key is encrypted with the newly received RSA-2048 public key and sent to the C&C server.
- The actual data exchange after the key exchange is then encrypted using symmetric cryptography, which is faster, with the AES-256 key
- The Potao malware sends an encrypted request to the server with computer ID, campaign ID, OS version, version of malware, computer name, current privileges, OS architecture (64 or 32bits) and also the name of the current process.
- Potao USB - uses social engineering, exe in the root disguised as drive icon
- Potao Anti RE - uses the MurmurHash2 algorithm for computing the hashes of the API function names.
- Potao Anti RE - encryption of strings
- Russian TrueCrypt Win32/FakeTC - The malicious program code within the otherwise functional TrueCrypt software runs in its own thread. This thread, created at the end of the Mount function, enumerates files on the mounted encrypted drive, and if certain conditions are met, it connects to the C&C server, ready to execute commands from the attackers.
------------------------------------------------------------------------------------------------------------------------
Original
Operation Potao Express: Analysis of a cyber-espionage toolkit
Attackers spying on high-value targets in Ukraine, Russia and Belarus, and their TrueCrypt-encrypted data
We presented our initial findings based on research into the Win32/Potao malware family in June, in our CCCC 2015 presentation in Copenhagen. Today, we are releasing the full whitepaper on the Potao malware with additional findings, the cyberespionage campaigns where it was employed, and its connection to a backdoor in the form of a modified version of the TrueCrypt encryption software.
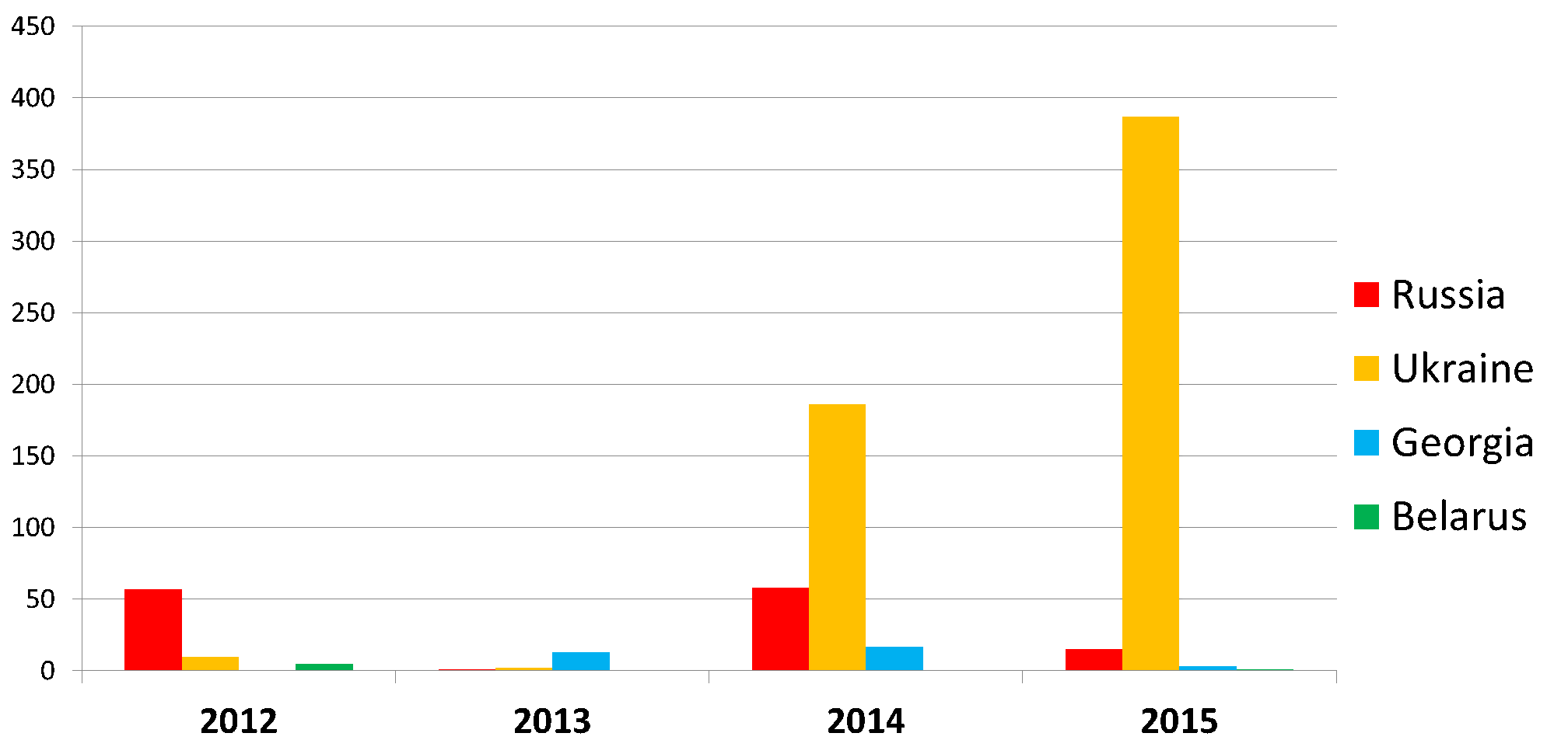
Like BlackEnergy, the malware used by the so-called Sandworm APT group (also known as Quedagh), Potao is an example of targeted espionage malware directed mostly at targets in Ukraine and a number of other post-Soviet countries, including Russia, Georgia and Belarus.

Figure 1- Detection statistics for Win32/Potao according to ESET LiveGrid®
Attack Timeline
The attacks conducted using the Win32/Potao malware family span the past 5 years, the first detections dating back to 2011. The attackers are, however, still very active, with the most recent infiltration attempts detected by ESET in July 2015.
The timeline below lists a selection of Potao attack campaigns and other related events.

Figure 2 – Timeline of selected Patao campaigns
Among the victims identified, the most notable high-value targets include Ukrainian government and military entities and one of the major Ukrainian news agencies. The malware was also used to spy on members of MMM, a Ponzi scheme popular in Russia and Ukraine.
Malware Techniques
When the criminals shifted their focus from attacking targets in Russia to others in Ukraine, they began sending personalized SMS messages to their potential victims to lure them to landing pages hosting the malware, disguised as postal tracking sites.
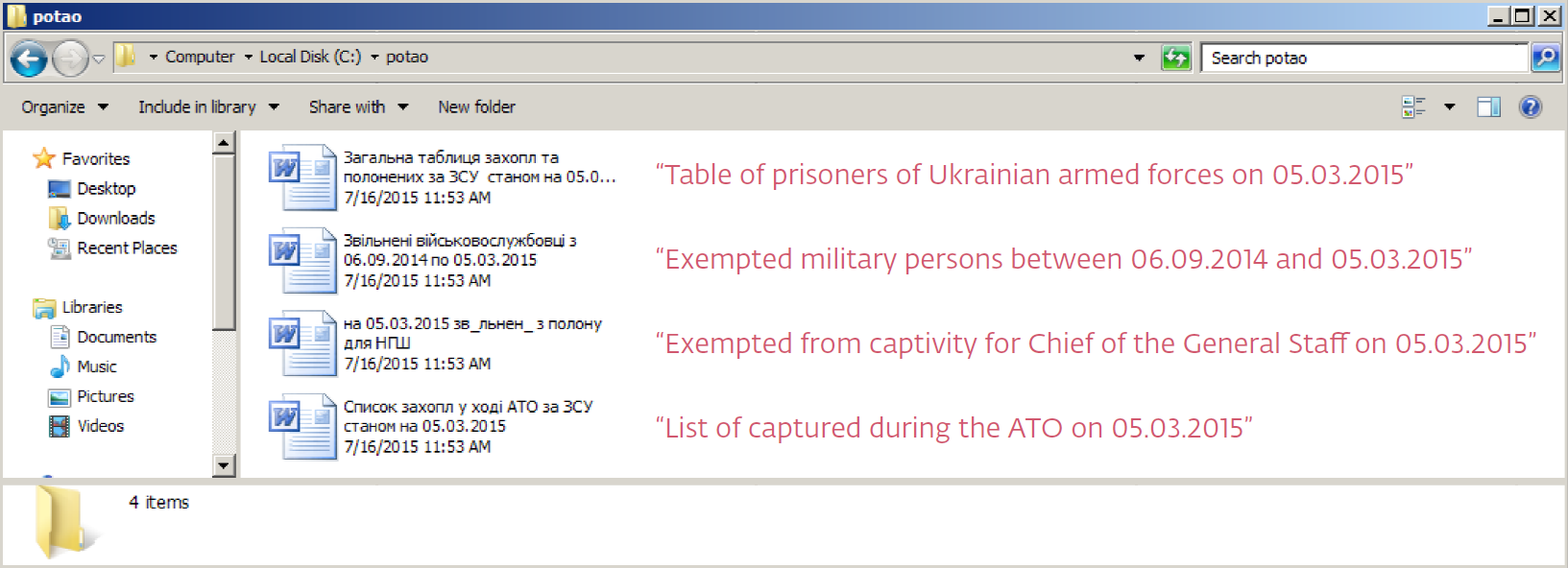
We haven’t noticed Win32/Potao employing any exploits and the malware isn’t particularly technically advanced. (Shouldn’t call it an APT then, right?) Yet it does contain a few other interesting techniques that ‘get the job done’, like the mechanism for spreading via USB drives and disguising executables as Word and Excel documents, as in the following examples:

Figure 3 – Potao droppers with MS Word icons and file names used in attacks against high-value Ukrainian targets to capture the interest of recipients
Trojanized TrueCrypt
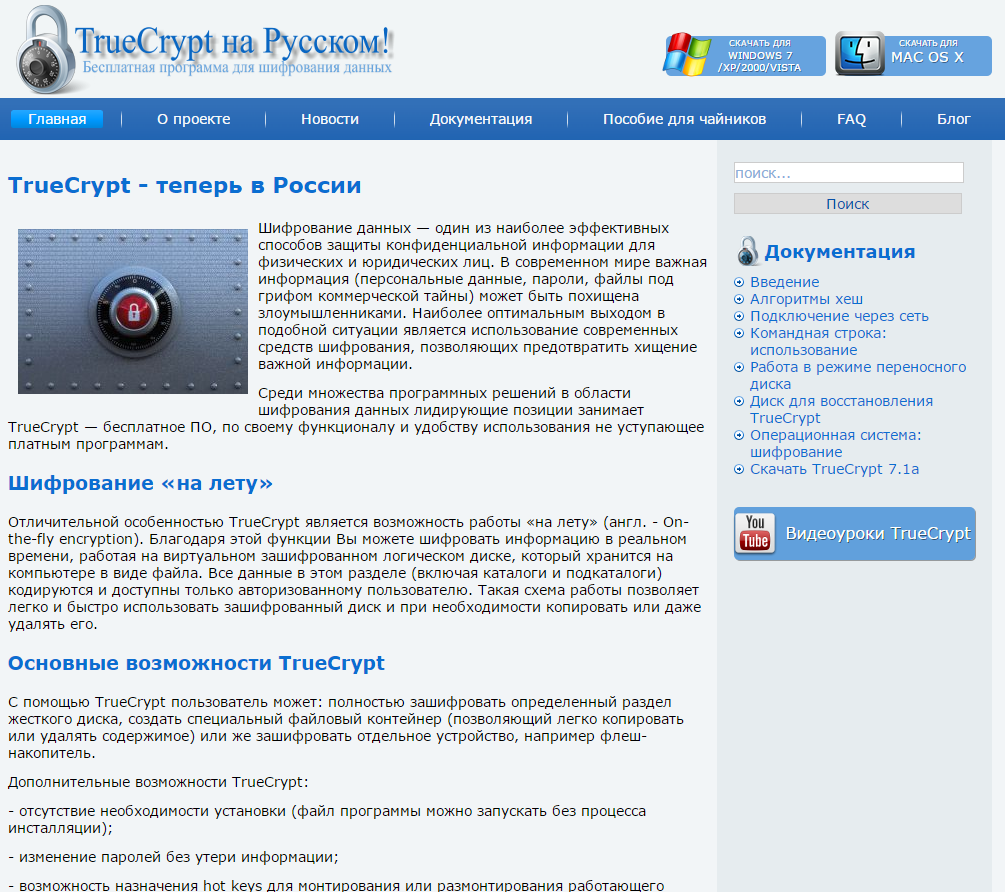
An (A)PT malware family that has gone relatively unnoticed for five years and that has also been used to spy on Ukrainian governmental and military targets is certainly interesting in and of itself. However, perhaps the most attention-grabbing discovery related to this case was when we observed a connection to the popular open-source encryption software, TrueCrypt.
We found out that the website truecryptrussia.ru has been serving modified versions of the encryption software that included a backdoor to selected targets. Clean versions of the application are served to normal visitors to the website, i.e. people who aren’t of interest to the attackers. ESET detects the trojanized TrueCrypt as Win32/FakeTC. TrueCrypt Russia’s domain was also used as a C&C server for the malware.

Figure 4 – TrueCrypt Russia’s Website
The connection to Win32/Potao, which is a different malware family from Win32/FakeTC, is that FakeTC has been used to deliver Potao to victims’ systems in a number of cases.
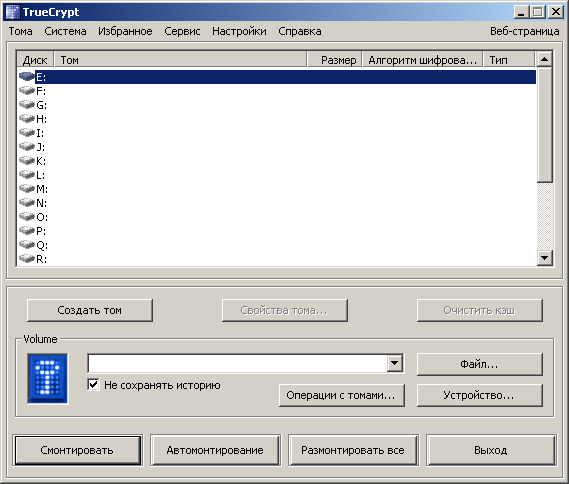
FakeTC is not, however, merely an infection vector for Potao (and possibly other malware) but a fully functional and dangerous backdoor designed to exfiltrate files from the espionage victims’ encrypted drives.

Figure 5 – Interface of the trojanized Russian TrueCrypt
In addition to the selective targeting (deciding to whom to serve the trojanized version instead of the clean one), the backdoor code also contained triggers that would only activate the malicious data-stealing functionality for active, long-term TrueCrypt users. These were surely contributing factors to the malware’s going unnoticed for such a long time.
Further details on both Win32/Potao and Win32/FakeTC, including a technical analysis of the malware, description of plugins, infection vectors, C&C communication protocol and other spreading campaigns not mentioned in this blog post are included in our comprehensive whitepaper.
Indicators of Compromise (IOC) that can be used to identify an infection can be found in the whitepaper or on github: https://github.com/eset/malware-ioc/tree/master/potao
Full Whitepaper
http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf
Operation Potao Indicators of Compromise (IOC)
These IOCs were released as part of our research on Operation Potao. The full report is available here: http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf
We have IOCs in the form of hashes, IP addresses, domain names, yara rules and IDS rules (snort). Hashes, IP addresses and domain names are documented here, the rest are in separate files inside this folder.
Caution
As soon as this information is public the malware authors will most likely update their technique and tools to evade detection and thwart analysis as they have done in the past. Consequently, be aware that any of the advice we give to identify or clean oneself might already be outdated.
Warning
These come with no warranties. They might not detect an infection and/or trigger false positives. Apply judgment.
If you find false-positives, have improved IOCs or find samples that do not match these IOCs please open an issue, provide a pull-request or contact us at: threatintel@eset.com.
Malware samples
The first version:
8839D3E213717B88A06FFC48827929891A10059E
5C52996D9F68BA6FD0DA4982F238EC1D279A7F9D
CE7F96B400ED51F7FAB465DEA26147984F2627BD
D88C7C1E465BEA7BF7377C08FBA3AAF77CBF485F
81EFB422ED2631C739CC690D0A9A5EAA07897531
18DDCD41DCCFBBD904347EA75BC9413FF6DC8786
E400E1DD983FD94E29345AABC77FADEB3F43C219
EB86615F539E35A8D3E4838949382D09743502BF
52E59CD4C864FBFC9902A144ED5E68C9DED45DEB
642BE4B2A87B47E77814744D154094392E413AB1
Debug versions:
BA35EDC3143AD021BB2490A3EB7B50C06F2EA40B
9D584DE2CCE6B654E62573938C2C824D7CC7D0EB
73A4A6864EF68C810C7C699ED51B759CF1C4ADFB
1B3437C06CF917920688B25DA0345749AA1A4A46
Droppers with decoy:
FBB399568E0A3B2E461A4EB3268ABDF07F3D5764
4D5E0808A03A75BFE8202E3A6D2920EDDBFC7774
BCC5A0CE0BCDFEA2FD1D64B5529EAC7309488273
F8BCDAD02DA2E0223F45F15DA4FBAB053E73CF6E
2CDD6AABB71FDB244BAA313EBBA13F06BCAD2612
9BE3800B49E84E0C014852977557F21BCDE2A775
4AC999A1C54AE6F54803023DC0FCF126CB77C854
59C07E5D69181E6C3AFA7593E26D33383722D6C5
E15834263F2A6CCAE07D106A71B99FE80A5F744B
A62E69EF1E4F4D48E2920572B9176AEDB0EEB1C6
900AD432B4CB2F2790FFEB0590B0A8348D9E60EB
856802E0BD4A774CFFFE5134D249508D89DCDA58
A655020D606CA180E056A5B2C2F72F94E985E9DB
Droppers from postal sites:
94BBF39FFF09B3A62A583C7D45A00B2492102DD7
F347DA9AAD52B717641AD3DD96925AB634CEB572
A4D685FCA8AFE9885DB75282516006F5BC56C098
CC9BDBE37CBAF0CC634076950FD32D9A377DE650
B0413EA5C5951C57EA7201DB8BB1D8C5EF42AA1E
0AE4E6E6FA1B1F8161A74525D4CB5A1808ABFAF4
EC0563CDE3FFAFF424B97D7EB692847132344127
639560488A75A9E3D35E4C0D9C4934295072DD89
USB-spreaders:
850C9F3B14F895AAA97A85AE147F07C9770FB4C7
BB0500A24853E404AD6CA708813F926B90B38468
71A5DA3CCB4347FE785C6BFFF7B741AF80B76091
7664C490160858EC8CFC8203F88D354AEA1CFE43
92A459E759320447E1FA7B0E48328AB2C20B2C64
BB7A089BAE3A4AF44FB9B053BB703239E03C036E
DB966220463DB87C2C51C19303B3A20F4577D632
37A3E77BFA6CA1AFBD0AF7661655815FB1D3DA83
181E9BCA23484156CAE005F421629DA56B5CC6B5
A96B3D31888D267D7488417AFE68671EB4F568BD
224A07F002E8DFB3F2B615B3FA71166CF1A61B6D
5D4724FBA02965916A15A50A6937CDB6AB609FDD
8BE74605D90ED762310241828340900D4B502358
5BE1AC1515DA2397A7C52A8B1DF384DD938FA714
56F6AC6197CE9CC774F72DF948B414EED576B6C3
F6F290A95D68373DA813782EF4723E39524D048B
48904399F7726B9ADF7F28C07B0599717F741B8B
791ECF11C04470E9EA881549AEBD1DDED3E4A5CA
E2B2B2C8FB1996F3A4A4E3CEE09028437A5284AE
5B30ECFD47988A77556FE6C0C0B950510052C91E
4EE82934F24E348696F1C813C24797618286A70C
B80A90B39FBA705F86676C5CC3E0DECA225D57FF
971A69547C5BC9B711A3BB6F6F2C5E3A46BF7B29
C1D8BE765ADCF76E5CCB2CF094191C0FEC4BF085
2531F40A1D9E50793D04D245FD6185AAEBCC54F4
Other droppers:
D8837002A04F4C93CC3B857F6A42CED6C9F3B882
BA5AD566A28D7712E0A64899D4675C06139F3FF0
FF6F6DCBEDC24D22541013D2273C63B5F0F19FE9
76DA7B4ABC9B711AB1EF87B97C61DD895E508232
855CA024AFBA0DC09D336A0896318D5CC47F03A6
12240271E928979AB2347C29B5599D6AC7CD6B8E
A9CB079EF49CEE35BF68AC80534CBFB5FA443780
1B278A1A5E109F32B526660087AEA99FB8D89403
4332A5AD314616D9319C248D41C7D1A709124DB2
5BEA9423DB6D0500920578C12CB127CBAFDD125E
Plugins:
2341139A0BC4BB80F5EFCE63A97AA9B5E818E79D
8BD2C45DE1BA7A7FD27E43ABD35AE30E0D5E03BC
54FEDCDB0D0F47453DD65373378D037844E813D0
CC3ECFB822D09CBB37916D7087EB032C1EE81AEE
F1C9BC7B1D3FD3D9D96ECDE3A46DFC3C33BBCD2B
9654B6EA49B7FEC4F92683863D10C045764CCA86
526C3263F63F9470D08C6BA23E68F030E76CAAF3
E6D2EF05CEDCD4ABF1D8E3BCAF48B768EAC598D7
CEBAB498E6FB1A324C84BA267A7BF5D9DF1CF264
324B65C4291696D5C6C29B299C2849261F816A08
C96C29252E24B3EEC5A21C29F7D9D30198F89232
CDDDE7D44EFE12B7252EA300362CF5898BDC5013
84A70CDC24B68207F015D6308FE5AD13DDABB771
Fake TrueCrypt Setup:
82F48D7787BDE5B7DEC046CBEF99963EEEB821A7
9666AF44FAFC37E074B79455D347C2801218D9EA
C02878A69EFDE20F049BC380DAE10133C32E9CC9
7FBABEA446206991945FB4586AEE93B61AF1B341
Fake TrueCrypt extracted exe:
DCBD43CFE2F490A569E1C3DD6BCA6546074FD2A1
422B350371B3666A0BD0D56AEAAD5DEC6BD7C0D0
88D703ADDB26ACB7FBE35EC04D7B1AA6DE982241
86E3276B03F9B92B47D441BCFBB913C6C4263BFE
Domain names
truecryptrussia.ru
mntexpress.com
worldairpost.com
worldairpost.net
camprainbowgold.ru
poolwaterslide2011.ru
IP addresses
78.47.218.234
95.86.129.92
115.68.23.192
67.18.208.92
37.139.47.162
212.227.137.245
62.76.189.181
87.106.44.200
62.76.42.14
94.242.199.78
178.239.60.96
84.234.71.215
67.103.159.141
62.76.184.245
83.169.20.47
148.251.33.219
98.129.238.97
195.210.28.105
198.136.24.155
46.165.228.130
192.154.97.239
5.44.99.46
188.240.46.1
81.196.48.188
74.54.206.162
69.64.72.206
74.208.68.243
46.163.73.99
193.34.144.63
103.3.77.219
119.59.105.221
188.40.71.188
188.40.71.137
108.179.245.41
64.40.101.43
190.228.169.253
194.15.126.123
188.127.249.19
Detection (YARA)
In order to identify if a file or a set of files are related to this threat you can use the popular yara tool.
Using the .yar Yara rule in this repository you can recursively crawl a directory for an Operation Potao file with:
yara -r PotaoNew.yar directory/
If the command yields no output then no files were identified to be of that threat. Otherwise identified filenames are printed.
Further modifications made by the malware authors to evade detection will impact the usefulness of this Yara rule over time.
Detection (IDS)
Snort rules are available in potao.rules.
Additionally, the fine folks at Emerging Threats designed Snort and Suricata rules to detect Operation Potao and included them in their open ruleset. You can also find them in this repository: potao-et.rules
private rule PotaoDecoy
{
strings:
$mz = { 4d 5a }
$str1 = "eroqw11"
$str2 = "2sfsdf"
$str3 = "RtlDecompressBuffer"
$wiki_str = "spanned more than 100 years and ruined three consecutive" wide
$old_ver1 = {53 68 65 6C 6C 33 32 2E 64 6C 6C 00 64 61 66 73 72 00 00 00 64 61 66 73 72 00 00 00 64 6F 63 (00 | 78)}
$old_ver2 = {6F 70 65 6E 00 00 00 00 64 6F 63 00 64 61 66 73 72 00 00 00 53 68 65 6C 6C 33 32 2E 64 6C 6C 00}
condition:
($mz at 0) and ( (all of ($str*)) or any of ($old_ver*) or $wiki_str )
}
private rule PotaoDll
{
strings:
$mz = { 4d 5a }
$dllstr1 = "?AVCncBuffer@@"
$dllstr2 = "?AVCncRequest@@"
$dllstr3 = "Petrozavodskaya, 11, 9"
$dllstr4 = "_Scan@0"
$dllstr5 = "\x00/sync/document/"
$dllstr6 = "\\temp.temp"
$dllname1 = "node69MainModule.dll"
$dllname2 = "node69-main.dll"
$dllname3 = "node69MainModuleD.dll"
$dllname4 = "task-diskscanner.dll"
$dllname5 = "\x00Screen.dll"
$dllname6 = "Poker2.dll"
$dllname7 = "PasswordStealer.dll"
$dllname8 = "KeyLog2Runner.dll"
$dllname9 = "GetAllSystemInfo.dll"
$dllname10 = "FilePathStealer.dll"
condition:
($mz at 0) and (any of ($dllstr*) and any of ($dllname*))
}
private rule PotaoUSB
{
strings:
$mz = { 4d 5a }
$binary1 = { 33 C0 8B C8 83 E1 03 BA ?? ?? ?? 00 2B D1 8A 0A 32 88 ?? ?? ?? 00 2A C8 FE C9 88 88 ?? ?? ?? 00 40 3D ?? ?? 00 00 7C DA C3 }
$binary2 = { 55 8B EC 51 56 C7 45 FC 00 00 00 00 EB 09 8B 45 FC 83 C0 01 89 45 FC 81 7D FC ?? ?? 00 00 7D 3D 8B 4D FC 0F BE 89 ?? ?? ?? 00 8B 45 FC 33 D2 BE 04 00 00 00 F7 F6 B8 03 00 00 00 2B C2 0F BE 90 ?? ?? ?? 00 33 CA 2B 4D FC 83 E9 01 81 E1 FF 00 00 00 8B 45 FC 88 88 ?? ?? ?? 00 EB B1 5E 8B E5 5D C3}
condition:
($mz at 0) and any of ($binary*)
}
private rule PotaoSecondStage
{
strings:
$mz = { 4d 5a }
// hash of CryptBinaryToStringA and CryptStringToBinaryA
$binary1 = {51 7A BB 85 [10-180] E8 47 D2 A8}
// old hash of CryptBinaryToStringA and CryptStringToBinaryA
$binary2 = {5F 21 63 DD [10-30] EC FD 33 02}
$binary3 = {CA 77 67 57 [10-30] BA 08 20 7A}
$str1 = "?AVCrypt32Import@@"
$str2 = "%.5llx"
condition:
($mz at 0) and any of ($binary*) and any of ($str*)
}
rule Potao
{
meta:
Author = "Anton Cherepanov"
Date = "2015/07/29"
Description = "Operation Potao"
Reference = "http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf"
Source = "https://github.com/eset/malware-ioc/"
Contact = "threatintel@eset.com"
License = "BSD 2-Clause"
condition:
PotaoDecoy or PotaoDll or PotaoUSB or PotaoSecondStage
}
alert tcp $HOME_NET any -> $EXTERNAL_NET [80,8008,8080] (msg:"ET TROJAN Win32/Potao HTTP CnC Beacon"; flow:established,to_server; content:"POST"; http_method; content:"/winter/task"; http_uri; fast_pattern; content:"Content-Type|3a| application/xml|0d 0a|"; http_header; content:"10a7d030-1a61-11e3-beea-001c42e2a08b"; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370001; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/FakeTC C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0f|truecryptrussia|02|ru|00|"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370002; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0a|mntexpress|03|com"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370003; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0c|worldairpost|03|com"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370004; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0c|worldairpost|03|net"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370005; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0f|camprainbowgold|02|ru"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370006; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|12|poolwaterslide2011|02|ru"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370007; rev:1;)alert ip $HOME_NET any -> 78.47.218.234 443 (msg:"ET TROJAN Win32/FakeTC Connection to C&C IP"; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370008; rev:1;)alert ip $HOME_NET any -> [95.86.129.92,115.68.23.192,67.18.208.92,37.139.47.162,212.227.137.245,62.76.189.181,87.106.44.200,62.76.42.14,94.242.199.78,178.239.60.96,84.234.71.215,67.103.159.141,62.76.184.245,83.169.20.47,148.251.33.219,98.129.238.97,195.210.28.105,198.136.24.155,46.165.228.130,192.154.97.239,5.44.99.46,188.240.46.1,81.196.48.188,74.54.206.162,69.64.72.206,74.208.68.243,46.163.73.99,193.34.144.63,103.3.77.219,119.59.105.221,188.40.71.188,188.40.71.137,108.179.245.41,64.40.101.43,190.228.169.253,194.15.126.123,188.127.249.19] [80,8008,8080,443] (msg:"ET TROJAN Win32/Potao Connection to C&C IP"; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370009; rev:1;)
These IOCs were released as part of our research on Operation Potao. The full report is available here: http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf
We have IOCs in the form of hashes, IP addresses, domain names, yara rules and IDS rules (snort). Hashes, IP addresses and domain names are documented here, the rest are in separate files inside this folder.
Caution
As soon as this information is public the malware authors will most likely update their technique and tools to evade detection and thwart analysis as they have done in the past. Consequently, be aware that any of the advice we give to identify or clean oneself might already be outdated.
Warning
These come with no warranties. They might not detect an infection and/or trigger false positives. Apply judgment.
If you find false-positives, have improved IOCs or find samples that do not match these IOCs please open an issue, provide a pull-request or contact us at: threatintel@eset.com.
Malware samples
The first version:
8839D3E213717B88A06FFC48827929891A10059E
5C52996D9F68BA6FD0DA4982F238EC1D279A7F9D
CE7F96B400ED51F7FAB465DEA26147984F2627BD
D88C7C1E465BEA7BF7377C08FBA3AAF77CBF485F
81EFB422ED2631C739CC690D0A9A5EAA07897531
18DDCD41DCCFBBD904347EA75BC9413FF6DC8786
E400E1DD983FD94E29345AABC77FADEB3F43C219
EB86615F539E35A8D3E4838949382D09743502BF
52E59CD4C864FBFC9902A144ED5E68C9DED45DEB
642BE4B2A87B47E77814744D154094392E413AB1
Debug versions:
BA35EDC3143AD021BB2490A3EB7B50C06F2EA40B
9D584DE2CCE6B654E62573938C2C824D7CC7D0EB
73A4A6864EF68C810C7C699ED51B759CF1C4ADFB
1B3437C06CF917920688B25DA0345749AA1A4A46
Droppers with decoy:
FBB399568E0A3B2E461A4EB3268ABDF07F3D5764
4D5E0808A03A75BFE8202E3A6D2920EDDBFC7774
BCC5A0CE0BCDFEA2FD1D64B5529EAC7309488273
F8BCDAD02DA2E0223F45F15DA4FBAB053E73CF6E
2CDD6AABB71FDB244BAA313EBBA13F06BCAD2612
9BE3800B49E84E0C014852977557F21BCDE2A775
4AC999A1C54AE6F54803023DC0FCF126CB77C854
59C07E5D69181E6C3AFA7593E26D33383722D6C5
E15834263F2A6CCAE07D106A71B99FE80A5F744B
A62E69EF1E4F4D48E2920572B9176AEDB0EEB1C6
900AD432B4CB2F2790FFEB0590B0A8348D9E60EB
856802E0BD4A774CFFFE5134D249508D89DCDA58
A655020D606CA180E056A5B2C2F72F94E985E9DB
Droppers from postal sites:
94BBF39FFF09B3A62A583C7D45A00B2492102DD7
F347DA9AAD52B717641AD3DD96925AB634CEB572
A4D685FCA8AFE9885DB75282516006F5BC56C098
CC9BDBE37CBAF0CC634076950FD32D9A377DE650
B0413EA5C5951C57EA7201DB8BB1D8C5EF42AA1E
0AE4E6E6FA1B1F8161A74525D4CB5A1808ABFAF4
EC0563CDE3FFAFF424B97D7EB692847132344127
639560488A75A9E3D35E4C0D9C4934295072DD89
USB-spreaders:
850C9F3B14F895AAA97A85AE147F07C9770FB4C7
BB0500A24853E404AD6CA708813F926B90B38468
71A5DA3CCB4347FE785C6BFFF7B741AF80B76091
7664C490160858EC8CFC8203F88D354AEA1CFE43
92A459E759320447E1FA7B0E48328AB2C20B2C64
BB7A089BAE3A4AF44FB9B053BB703239E03C036E
DB966220463DB87C2C51C19303B3A20F4577D632
37A3E77BFA6CA1AFBD0AF7661655815FB1D3DA83
181E9BCA23484156CAE005F421629DA56B5CC6B5
A96B3D31888D267D7488417AFE68671EB4F568BD
224A07F002E8DFB3F2B615B3FA71166CF1A61B6D
5D4724FBA02965916A15A50A6937CDB6AB609FDD
8BE74605D90ED762310241828340900D4B502358
5BE1AC1515DA2397A7C52A8B1DF384DD938FA714
56F6AC6197CE9CC774F72DF948B414EED576B6C3
F6F290A95D68373DA813782EF4723E39524D048B
48904399F7726B9ADF7F28C07B0599717F741B8B
791ECF11C04470E9EA881549AEBD1DDED3E4A5CA
E2B2B2C8FB1996F3A4A4E3CEE09028437A5284AE
5B30ECFD47988A77556FE6C0C0B950510052C91E
4EE82934F24E348696F1C813C24797618286A70C
B80A90B39FBA705F86676C5CC3E0DECA225D57FF
971A69547C5BC9B711A3BB6F6F2C5E3A46BF7B29
C1D8BE765ADCF76E5CCB2CF094191C0FEC4BF085
2531F40A1D9E50793D04D245FD6185AAEBCC54F4
Other droppers:
D8837002A04F4C93CC3B857F6A42CED6C9F3B882
BA5AD566A28D7712E0A64899D4675C06139F3FF0
FF6F6DCBEDC24D22541013D2273C63B5F0F19FE9
76DA7B4ABC9B711AB1EF87B97C61DD895E508232
855CA024AFBA0DC09D336A0896318D5CC47F03A6
12240271E928979AB2347C29B5599D6AC7CD6B8E
A9CB079EF49CEE35BF68AC80534CBFB5FA443780
1B278A1A5E109F32B526660087AEA99FB8D89403
4332A5AD314616D9319C248D41C7D1A709124DB2
5BEA9423DB6D0500920578C12CB127CBAFDD125E
Plugins:
2341139A0BC4BB80F5EFCE63A97AA9B5E818E79D
8BD2C45DE1BA7A7FD27E43ABD35AE30E0D5E03BC
54FEDCDB0D0F47453DD65373378D037844E813D0
CC3ECFB822D09CBB37916D7087EB032C1EE81AEE
F1C9BC7B1D3FD3D9D96ECDE3A46DFC3C33BBCD2B
9654B6EA49B7FEC4F92683863D10C045764CCA86
526C3263F63F9470D08C6BA23E68F030E76CAAF3
E6D2EF05CEDCD4ABF1D8E3BCAF48B768EAC598D7
CEBAB498E6FB1A324C84BA267A7BF5D9DF1CF264
324B65C4291696D5C6C29B299C2849261F816A08
C96C29252E24B3EEC5A21C29F7D9D30198F89232
CDDDE7D44EFE12B7252EA300362CF5898BDC5013
84A70CDC24B68207F015D6308FE5AD13DDABB771
Fake TrueCrypt Setup:
82F48D7787BDE5B7DEC046CBEF99963EEEB821A7
9666AF44FAFC37E074B79455D347C2801218D9EA
C02878A69EFDE20F049BC380DAE10133C32E9CC9
7FBABEA446206991945FB4586AEE93B61AF1B341
Fake TrueCrypt extracted exe:
DCBD43CFE2F490A569E1C3DD6BCA6546074FD2A1
422B350371B3666A0BD0D56AEAAD5DEC6BD7C0D0
88D703ADDB26ACB7FBE35EC04D7B1AA6DE982241
86E3276B03F9B92B47D441BCFBB913C6C4263BFE
Domain names
truecryptrussia.ru
mntexpress.com
worldairpost.com
worldairpost.net
camprainbowgold.ru
poolwaterslide2011.ru
IP addresses
78.47.218.234
95.86.129.92
115.68.23.192
67.18.208.92
37.139.47.162
212.227.137.245
62.76.189.181
87.106.44.200
62.76.42.14
94.242.199.78
178.239.60.96
84.234.71.215
67.103.159.141
62.76.184.245
83.169.20.47
148.251.33.219
98.129.238.97
195.210.28.105
198.136.24.155
46.165.228.130
192.154.97.239
5.44.99.46
188.240.46.1
81.196.48.188
74.54.206.162
69.64.72.206
74.208.68.243
46.163.73.99
193.34.144.63
103.3.77.219
119.59.105.221
188.40.71.188
188.40.71.137
108.179.245.41
64.40.101.43
190.228.169.253
194.15.126.123
188.127.249.19
Detection (YARA)
In order to identify if a file or a set of files are related to this threat you can use the popular yara tool.
Using the .yar Yara rule in this repository you can recursively crawl a directory for an Operation Potao file with:
yara -r PotaoNew.yar directory/
If the command yields no output then no files were identified to be of that threat. Otherwise identified filenames are printed.
Further modifications made by the malware authors to evade detection will impact the usefulness of this Yara rule over time.
Detection (IDS)
Snort rules are available in potao.rules.
Additionally, the fine folks at Emerging Threats designed Snort and Suricata rules to detect Operation Potao and included them in their open ruleset. You can also find them in this repository: potao-et.rules
private rule PotaoDecoy
{
strings:
$mz = { 4d 5a }
$str1 = "eroqw11"
$str2 = "2sfsdf"
$str3 = "RtlDecompressBuffer"
$wiki_str = "spanned more than 100 years and ruined three consecutive" wide
$old_ver1 = {53 68 65 6C 6C 33 32 2E 64 6C 6C 00 64 61 66 73 72 00 00 00 64 61 66 73 72 00 00 00 64 6F 63 (00 | 78)}
$old_ver2 = {6F 70 65 6E 00 00 00 00 64 6F 63 00 64 61 66 73 72 00 00 00 53 68 65 6C 6C 33 32 2E 64 6C 6C 00}
condition:
($mz at 0) and ( (all of ($str*)) or any of ($old_ver*) or $wiki_str )
}
private rule PotaoDll
{
strings:
$mz = { 4d 5a }
$dllstr1 = "?AVCncBuffer@@"
$dllstr2 = "?AVCncRequest@@"
$dllstr3 = "Petrozavodskaya, 11, 9"
$dllstr4 = "_Scan@0"
$dllstr5 = "\x00/sync/document/"
$dllstr6 = "\\temp.temp"
$dllname1 = "node69MainModule.dll"
$dllname2 = "node69-main.dll"
$dllname3 = "node69MainModuleD.dll"
$dllname4 = "task-diskscanner.dll"
$dllname5 = "\x00Screen.dll"
$dllname6 = "Poker2.dll"
$dllname7 = "PasswordStealer.dll"
$dllname8 = "KeyLog2Runner.dll"
$dllname9 = "GetAllSystemInfo.dll"
$dllname10 = "FilePathStealer.dll"
condition:
($mz at 0) and (any of ($dllstr*) and any of ($dllname*))
}
private rule PotaoUSB
{
strings:
$mz = { 4d 5a }
$binary1 = { 33 C0 8B C8 83 E1 03 BA ?? ?? ?? 00 2B D1 8A 0A 32 88 ?? ?? ?? 00 2A C8 FE C9 88 88 ?? ?? ?? 00 40 3D ?? ?? 00 00 7C DA C3 }
$binary2 = { 55 8B EC 51 56 C7 45 FC 00 00 00 00 EB 09 8B 45 FC 83 C0 01 89 45 FC 81 7D FC ?? ?? 00 00 7D 3D 8B 4D FC 0F BE 89 ?? ?? ?? 00 8B 45 FC 33 D2 BE 04 00 00 00 F7 F6 B8 03 00 00 00 2B C2 0F BE 90 ?? ?? ?? 00 33 CA 2B 4D FC 83 E9 01 81 E1 FF 00 00 00 8B 45 FC 88 88 ?? ?? ?? 00 EB B1 5E 8B E5 5D C3}
condition:
($mz at 0) and any of ($binary*)
}
private rule PotaoSecondStage
{
strings:
$mz = { 4d 5a }
// hash of CryptBinaryToStringA and CryptStringToBinaryA
$binary1 = {51 7A BB 85 [10-180] E8 47 D2 A8}
// old hash of CryptBinaryToStringA and CryptStringToBinaryA
$binary2 = {5F 21 63 DD [10-30] EC FD 33 02}
$binary3 = {CA 77 67 57 [10-30] BA 08 20 7A}
$str1 = "?AVCrypt32Import@@"
$str2 = "%.5llx"
condition:
($mz at 0) and any of ($binary*) and any of ($str*)
}
rule Potao
{
meta:
Author = "Anton Cherepanov"
Date = "2015/07/29"
Description = "Operation Potao"
Reference = "http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf"
Source = "https://github.com/eset/malware-ioc/"
Contact = "threatintel@eset.com"
License = "BSD 2-Clause"
condition:
PotaoDecoy or PotaoDll or PotaoUSB or PotaoSecondStage
}
alert tcp $HOME_NET any -> $EXTERNAL_NET [80,8008,8080] (msg:"ET TROJAN Win32/Potao HTTP CnC Beacon"; flow:established,to_server; content:"POST"; http_method; content:"/winter/task"; http_uri; fast_pattern; content:"Content-Type|3a| application/xml|0d 0a|"; http_header; content:"10a7d030-1a61-11e3-beea-001c42e2a08b"; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370001; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/FakeTC C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0f|truecryptrussia|02|ru|00|"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370002; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0a|mntexpress|03|com"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370003; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0c|worldairpost|03|com"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370004; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0c|worldairpost|03|net"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370005; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|0f|camprainbowgold|02|ru"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370006; rev:1;)alert udp any any -> any 53 (msg:"ET TROJAN Win32/Potao C&C DNS request"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|12|poolwaterslide2011|02|ru"; fast_pattern; nocase; distance:0; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370007; rev:1;)alert ip $HOME_NET any -> 78.47.218.234 443 (msg:"ET TROJAN Win32/FakeTC Connection to C&C IP"; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370008; rev:1;)alert ip $HOME_NET any -> [95.86.129.92,115.68.23.192,67.18.208.92,37.139.47.162,212.227.137.245,62.76.189.181,87.106.44.200,62.76.42.14,94.242.199.78,178.239.60.96,84.234.71.215,67.103.159.141,62.76.184.245,83.169.20.47,148.251.33.219,98.129.238.97,195.210.28.105,198.136.24.155,46.165.228.130,192.154.97.239,5.44.99.46,188.240.46.1,81.196.48.188,74.54.206.162,69.64.72.206,74.208.68.243,46.163.73.99,193.34.144.63,103.3.77.219,119.59.105.221,188.40.71.188,188.40.71.137,108.179.245.41,64.40.101.43,190.228.169.253,194.15.126.123,188.127.249.19] [80,8008,8080,443] (msg:"ET TROJAN Win32/Potao Connection to C&C IP"; reference:url,http://www.welivesecurity.com/wp-content/uploads/2015/07/Operation-Potao-Express_final_v2.pdf; reference:url,github.com/eset/malware-ioc; classtype:trojan-activity; sid:35370009; rev:1;)

